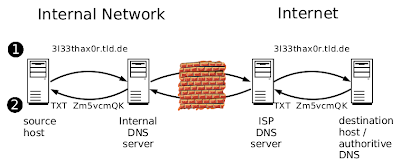
dns sock proxy or DNS Tunnel is you make a hole on dns server by create your own dns to reply dns asking. Lets see
by the picture, you can see what you need are :
lets start :
$ sudo apt-get install iodine
[sudo] password for febru:
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following packages were automatically installed and are no longer required:
lib32gcc1 lib32stdc++6 libc6-i386
Use 'apt-get autoremove' to remove them.
Suggested packages:
fping oping gawk ipcalc
The following NEW packages will be installed:
iodine
febru@tiago:~$ sudo iodined -f 10.0.0.1 -P pwd redirect0.chickenkiller.com
Opened dns0
Setting IP of dns0 to 10.0.0.1
Setting MTU of dns0 to 1130
Opened UDP socket
Listening to dns for domain redirect0.chickenkiller.com
febru@sevilla:~$ sudo iodine -f -r server -P pwd redirect0.chickenkiller.com
Opened dns0
Opened UDP socket
Sending DNS queries for redirect0.chickenkiller.com to server
Autodetecting DNS query type (use -T to override)...
Using DNS type NULL queries
Version ok, both using protocol v 0x00000502. You are user #0
Setting IP of dns0 to 10.0.0.2
Setting MTU of dns0 to 1130
Server tunnel IP is 10.0.0.1
Skipping raw mode
Using EDNS0 extension
Switching upstream to codec Base128
Server switched upstream to codec Base128
No alternative downstream codec available, using default (Raw)
Switching to lazy mode for low-latency
Server switched to lazy mode
Autoprobing max downstream fragment size... (skip with -m fragsize)
768 ok.. ...1152 not ok.. 960 ok.. 1056 ok.. 1104 ok.. 1128 ok.. 1140 ok.. will use 1140-2=1138
Setting downstream fragment size to max 1138...
Connection setup complete, transmitting data.
febru@sevilla:~$ ifconfig
dns0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.0.0.2 P-t-P:10.0.0.2 Mask:255.255.255.224
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1130 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:500
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
febru@sevilla:~$ ssh -qTfnN2 -D 8080 febru@10.0.0.1
The authenticity of host '10.0.0.1 (10.0.0.1)' can't be established.
RSA key fingerprint is 60:b3:a2:6b:3d:f7:d1:a6:98:7b:13:8c:ea:98:66:35.
Are you sure you want to continue connecting (yes/no)? yes
febru@10.0.0.1's password:
by the picture, you can see what you need are :
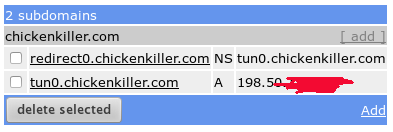
- your own subDomain. Create your own sub domain on your dns server (in internet, let say your new NS is test.com). you can see here to setup your sub domain.
- your isp DNS server is allow to send data, you can test by ping to some site, or official website of your internet provider.
lets start :
install iodine on ubuntu 13.10.
your client (laptop) and server (dns server)$ sudo apt-get install iodine
[sudo] password for febru:
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following packages were automatically installed and are no longer required:
lib32gcc1 lib32stdc++6 libc6-i386
Use 'apt-get autoremove' to remove them.
Suggested packages:
fping oping gawk ipcalc
The following NEW packages will be installed:
iodine
Domain lookup on ubuntu 13.10.
$ dig A test.com +short
208.64.121.161
from your dns test, you can see that your dns ip was reached with IP 208.64.121.161
setup iodine.
on server :
iodined -f 10.0.0.1 -P your_secret_password my_sub_domain.test.com
febru@tiago:~$ sudo iodined -f 10.0.0.1 -P pwd redirect0.chickenkiller.com
Opened dns0
Setting IP of dns0 to 10.0.0.1
Setting MTU of dns0 to 1130
Opened UDP socket
Listening to dns for domain redirect0.chickenkiller.com
on client
sudo iodine -f -r 208.64.121.161 -P your_secret_password my_sub_domain.test.com
febru@sevilla:~$ sudo iodine -f -r server -P pwd redirect0.chickenkiller.com
Opened dns0
Opened UDP socket
Sending DNS queries for redirect0.chickenkiller.com to server
Autodetecting DNS query type (use -T to override)...
Using DNS type NULL queries
Version ok, both using protocol v 0x00000502. You are user #0
Setting IP of dns0 to 10.0.0.2
Setting MTU of dns0 to 1130
Server tunnel IP is 10.0.0.1
Skipping raw mode
Using EDNS0 extension
Switching upstream to codec Base128
Server switched upstream to codec Base128
No alternative downstream codec available, using default (Raw)
Switching to lazy mode for low-latency
Server switched to lazy mode
Autoprobing max downstream fragment size... (skip with -m fragsize)
768 ok.. ...1152 not ok.. 960 ok.. 1056 ok.. 1104 ok.. 1128 ok.. 1140 ok.. will use 1140-2=1138
Setting downstream fragment size to max 1138...
Connection setup complete, transmitting data.
febru@sevilla:~$ ifconfig
dns0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.0.0.2 P-t-P:10.0.0.2 Mask:255.255.255.224
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1130 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:500
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
the last, test your traffic now
ping 10.0.0.1
now you are connected to internet via port 53 (DNS Port), if you want to use this connection to browsing or others, you can use ssh tunnel and install squid proxy or you can use sock proxy tunnel without install squid proxy
febru@sevilla:~$ ssh -qTfnN2 -D 8080 febru@10.0.0.1
The authenticity of host '10.0.0.1 (10.0.0.1)' can't be established.
RSA key fingerprint is 60:b3:a2:6b:3d:f7:d1:a6:98:7b:13:8c:ea:98:66:35.
Are you sure you want to continue connecting (yes/no)? yes
febru@10.0.0.1's password:
note on using iodine.
- it will reject data / ping that not been active for more than 60 second, so you need to reconnect if idle more than 60 seconds. make other console-window to send ping continuously.
- iodine is just a big pipe to make main connection on dns port, if you want to setup dns tunneling one package with dynamic sock proxy, you can use ozymandns
after this, you can try icmp tunneling or ping tunneling or proxy ping
..show all:.
.
dns sock proxy or DNS Tunnel is you make a hole on dns server by create your own dns to reply dns asking. Lets see
by the picture, you can see what you need are :
lets start :
$ sudo apt-get install iodine
[sudo] password for febru:
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following packages were automatically installed and are no longer required:
lib32gcc1 lib32stdc++6 libc6-i386
Use 'apt-get autoremove' to remove them.
Suggested packages:
fping oping gawk ipcalc
The following NEW packages will be installed:
iodine
febru@tiago:~$ sudo iodined -f 10.0.0.1 -P pwd redirect0.chickenkiller.com
Opened dns0
Setting IP of dns0 to 10.0.0.1
Setting MTU of dns0 to 1130
Opened UDP socket
Listening to dns for domain redirect0.chickenkiller.com
febru@sevilla:~$ sudo iodine -f -r server -P pwd redirect0.chickenkiller.com
Opened dns0
Opened UDP socket
Sending DNS queries for redirect0.chickenkiller.com to server
Autodetecting DNS query type (use -T to override)...
Using DNS type NULL queries
Version ok, both using protocol v 0x00000502. You are user #0
Setting IP of dns0 to 10.0.0.2
Setting MTU of dns0 to 1130
Server tunnel IP is 10.0.0.1
Skipping raw mode
Using EDNS0 extension
Switching upstream to codec Base128
Server switched upstream to codec Base128
No alternative downstream codec available, using default (Raw)
Switching to lazy mode for low-latency
Server switched to lazy mode
Autoprobing max downstream fragment size... (skip with -m fragsize)
768 ok.. ...1152 not ok.. 960 ok.. 1056 ok.. 1104 ok.. 1128 ok.. 1140 ok.. will use 1140-2=1138
Setting downstream fragment size to max 1138...
Connection setup complete, transmitting data.
febru@sevilla:~$ ifconfig
dns0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.0.0.2 P-t-P:10.0.0.2 Mask:255.255.255.224
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1130 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:500
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
febru@sevilla:~$ ssh -qTfnN2 -D 8080 febru@10.0.0.1
The authenticity of host '10.0.0.1 (10.0.0.1)' can't be established.
RSA key fingerprint is 60:b3:a2:6b:3d:f7:d1:a6:98:7b:13:8c:ea:98:66:35.
Are you sure you want to continue connecting (yes/no)? yes
febru@10.0.0.1's password:
by the picture, you can see what you need are :
- your own subDomain. Create your own sub domain on your dns server (in internet, let say your new NS is test.com). you can see here to setup your sub domain.
- your isp DNS server is allow to send data, you can test by ping to some site, or official website of your internet provider.
lets start :
install iodine on ubuntu 13.10.
your client (laptop) and server (dns server)$ sudo apt-get install iodine
[sudo] password for febru:
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following packages were automatically installed and are no longer required:
lib32gcc1 lib32stdc++6 libc6-i386
Use 'apt-get autoremove' to remove them.
Suggested packages:
fping oping gawk ipcalc
The following NEW packages will be installed:
iodine
Domain lookup on ubuntu 13.10.
$ dig A test.com +short
208.64.121.161
from your dns test, you can see that your dns ip was reached with IP 208.64.121.161
setup iodine.
on server :
iodined -f 10.0.0.1 -P your_secret_password my_sub_domain.test.com
febru@tiago:~$ sudo iodined -f 10.0.0.1 -P pwd redirect0.chickenkiller.com
Opened dns0
Setting IP of dns0 to 10.0.0.1
Setting MTU of dns0 to 1130
Opened UDP socket
Listening to dns for domain redirect0.chickenkiller.com
on client
sudo iodine -f -r 208.64.121.161 -P your_secret_password my_sub_domain.test.com
febru@sevilla:~$ sudo iodine -f -r server -P pwd redirect0.chickenkiller.com
Opened dns0
Opened UDP socket
Sending DNS queries for redirect0.chickenkiller.com to server
Autodetecting DNS query type (use -T to override)...
Using DNS type NULL queries
Version ok, both using protocol v 0x00000502. You are user #0
Setting IP of dns0 to 10.0.0.2
Setting MTU of dns0 to 1130
Server tunnel IP is 10.0.0.1
Skipping raw mode
Using EDNS0 extension
Switching upstream to codec Base128
Server switched upstream to codec Base128
No alternative downstream codec available, using default (Raw)
Switching to lazy mode for low-latency
Server switched to lazy mode
Autoprobing max downstream fragment size... (skip with -m fragsize)
768 ok.. ...1152 not ok.. 960 ok.. 1056 ok.. 1104 ok.. 1128 ok.. 1140 ok.. will use 1140-2=1138
Setting downstream fragment size to max 1138...
Connection setup complete, transmitting data.
febru@sevilla:~$ ifconfig
dns0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.0.0.2 P-t-P:10.0.0.2 Mask:255.255.255.224
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1130 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:500
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
the last, test your traffic now
ping 10.0.0.1
now you are connected to internet via port 53 (DNS Port), if you want to use this connection to browsing or others, you can use ssh tunnel and install squid proxy or you can use sock proxy tunnel without install squid proxy
febru@sevilla:~$ ssh -qTfnN2 -D 8080 febru@10.0.0.1
The authenticity of host '10.0.0.1 (10.0.0.1)' can't be established.
RSA key fingerprint is 60:b3:a2:6b:3d:f7:d1:a6:98:7b:13:8c:ea:98:66:35.
Are you sure you want to continue connecting (yes/no)? yes
febru@10.0.0.1's password:
note on using iodine.
- it will reject data / ping that not been active for more than 60 second, so you need to reconnect if idle more than 60 seconds. make other console-window to send ping continuously.
- iodine is just a big pipe to make main connection on dns port, if you want to setup dns tunneling one package with dynamic sock proxy, you can use ozymandns
after this, you can try icmp tunneling or ping tunneling or proxy ping
Very informative post! There is a lot of information here that can help any business get started with a successful social networking campaign. diebestenvpn
ReplyDelete